Following are examples of HIPAA violations that took place in 2017. Each one is a nightmare that healthcare organizations should hope to avoid. The average drop in revenue at a healthcare provider after a data breach is almost $4 million, and that kind of breach is overwhelming.
- In April of 2017, Augusta University Medical Center reported that it had become a victim of phishing for the second time within a twelve-month period.
- In June of 2017, ransomware brought down Pacific Alliance Medical Center, which the firm said the attack impacted 266,123 of their patients.
- In July of 2017, a successful breach of Medical Oncology Hematology Consultants was detected, which compromised 19,203 patient records.
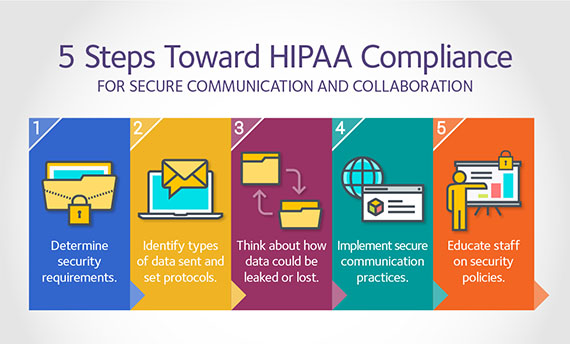
Unfortunately data breaches are more common and costly than many healthcare providers would like to think. Let’s review some fundamental security practices for protecting HIPAA-compliant data. Following are some tips your company can integrate to help secure protected health information that is your responsibility:
Training is fundamental.
It is imperative that you properly train your staff. Phishing campaigns, which is the attempt to obtain sensitive information, by disguising as a trustworthy entity in an electronic communication were created to create devastating mistakes from employees. It’s frightening that something as simple as a fake email could create a point of entry for attackers to exploit. Remember that people make mistakes, so be sure that you have security controls in place that prevent employees from inadvertently installing malware.
Encrypt everything.
Encrypting information means that even if your digital information is stolen, the encryption makes that information is unusable.
Assess your risk.
Conduct a comprehensive risk assessment of all the elements that store, process, or transfer electronic protected health information being gathered at your office. Make sure to evaluate the ways in which your information could be exposed.
Be vigilant and ready to act.
It is stressful knowing there is always a possibility of a data breach, but it is critical to be prepared for such a breach. A thoroughly planned, but easy to execute response needs to be designed. The Office for Civil Rights’ checklist lists the steps of a proper response after a breach of HIPAA-protected material:
- Stop the attack and contain the threat to privacy and security.
- Carry out your response and mitigation steps.
- Report the incident to law enforcement.
- Submit the relevant cyber threat indicators to federal and information sharing and analysis organizations.
- Notify the Office for Civil Rights quickly, within 60 days following the detection of a breach that compromised at least 500 people.
If you have any questions, please feel free to contact RevPro Healthcare Solutions below or call us at 561-578-8400.
Share this article: